Here are the basic configuration on implementing different types of Network Address Translation (NAT) on Cisco Routers.
Fig.1
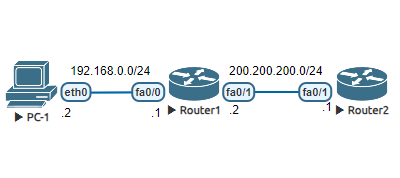
- Static NAT (1-to-1 Translation)
(Objective: to translate PC-1 private IP of 192.168.0.2 to public IP 200.200.200.3)
Configuration:
Router1
Main Static NAT configuration:
ip nat inside source static <Inside local IP> <Inside global IP>
Sample Config:
Router1(config)# ip nat inside source static 192.168.0.2 200.200.200.3
interface FastEthernet0/0
description Connection to PC-1
ip address 192.168.0.1 255.255.255.0
ip nat insideinterface FastEthernet0/1
description Connection to Router2
ip address 200.200.200.2 255.255.255.0
ip nat outside
Router2:
interface FastEthernet0/1
description Connection to Router1
ip address 200.200.200.1 255.255.255.0
Verification:
show ip nat translations
show ip nat statistics
show ip arp
Sample Output:
Router1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
— 200.200.200.3 192.168.0.2 — —
Router1#show ip nat statistics
Total active translations: 1 (1 static, 0 dynamic; 0 extended)
Outside interfaces:
FastEthernet0/1
Inside interfaces:
FastEthernet0/0
Hits: 29 Misses: 0
CEF Translated packets: 29, CEF Punted packets: 0
Expired translations: 1
Dynamic mappings:
Appl doors: 0
Normal doors: 0
Queued Packets: 0
Router1#show ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.0.1 – c219.3460.0000 ARPA FastEthernet0/0
Internet 192.168.0.2 39 0050.7966.681a ARPA FastEthernet0/0
Internet 200.200.200.1 39 c21b.335c.0001 ARPA FastEthernet0/1
Internet 200.200.200.2 – c219.3460.0001 ARPA FastEthernet0/1
Internet 200.200.200.3 – c219.3460.0001 ARPA FastEthernet0/1
2. Dynamic NAT (multiple private IP to pool of public IP)
Using the Fig.1 diagram
a. Configure access-list (ACL)
access-list <1-99> permit <address> <wildcard bits>
b. Configure NAT public IP pool
ip nat pool <Pool Name> <Start IP> <End IP> netmask <network mask>
c. Configure Dynamic NAT
ip nat inside source list <ACL number> pool <Pool name>
d. Configure router interfaces as inside or outside.
interface <interface name>
ip nat insideinterface <interface name>
ip nat outside
Sample Configuration:
Router1:
access-list 88 permit 192.168.0.0 0.0.0.255
ip nat pool POOL1 200.200.200.100 200.200.200.150 netmask 255.255.255.0
ip nat inside source list 88 pool POOL1
interface fa0/0
ip nat inside
interface fa0/1
ip nat outside
Sample Verification:
Router1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
— 200.200.200.100 192.168.0.2 — —
Router1#show ip nat statistics
Total active translations: 1 (0 static, 1 dynamic; 0 extended)
Outside interfaces:
FastEthernet0/1
Inside interfaces:
FastEthernet0/0
Hits: 37 Misses: 0
CEF Translated packets: 37, CEF Punted packets: 0
Expired translations: 6
Dynamic mappings:
— Inside Source
[Id: 3] access-list 88 pool POOL1 refcount 1
pool POOL1: netmask 255.255.255.0
start 200.200.200.100 end 200.200.200.150
type generic, total addresses 51, allocated 1 (1%), misses 0
Appl doors: 0
Normal doors: 0
Queued Packets: 0
Router1#show ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.0.1 – c219.3460.0000 ARPA FastEthernet0/0
Internet 192.168.0.2 9 0050.7966.681a ARPA FastEthernet0/0
Internet 200.200.200.1 9 c21b.335c.0001 ARPA FastEthernet0/1
Internet 200.200.200.2 – c219.3460.0001 ARPA FastEthernet0/1
Internet 200.200.200.100 – c219.3460.0001 ARPA FastEthernet0/1
3. Port Address Translation (NAT Overload) (multiple private IPs to single public IP)
Using the Fig.1 diagram
a. Configure access-list (ACL)
access-list <1-99> permit <address> <wildcard bits>
b. Configure NAT public IP pool (Optional)
ip nat pool <Pool Name> <Start IP> <End IP> netmask <network mask>
c. Configure Dynamic NAT Overload (PAT)
ip nat inside source list <ACL number> pool <Pool name> overload
or
ip nat inside source list <ACL number> interface <interface name> overload
d. Configure router interfaces as inside or outside.
interface <interface name>
ip nat insideinterface <interface name>
ip nat outside
Sample Configuration:
Router1:
access-list 88 permit 192.168.0.0 0.0.0.255
ip nat pool POOL1 200.200.200.2 200.200.200.2 netmask 255.255.255.0
ip nat inside source list 88 pool POOL1 overload
*or
ip nat inside source list 88 interface FastEthernet0/1 overload
interface fa0/0
ip nat inside
interface fa0/1
ip nat outside
Sample Verification:
Router1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 200.200.200.2:26983 192.168.0.2:26983 200.200.200.1:26983 200.200.200.1:26983
icmp 200.200.200.2:27495 192.168.0.2:27495 200.200.200.1:27495 200.200.200.1:27495
icmp 200.200.200.2:28007 192.168.0.2:28007 200.200.200.1:28007 200.200.200.1:28007
icmp 200.200.200.2:28519 192.168.0.2:28519 200.200.200.1:28519 200.200.200.1:28519
icmp 200.200.200.2:29031 192.168.0.2:29031 200.200.200.1:29031 200.200.200.1:29031
Router1#show ip nat statistics
Total active translations: 5 (0 static, 5 dynamic; 5 extended)
Outside interfaces:
FastEthernet0/1
Inside interfaces:
FastEthernet0/0
Hits: 52 Misses: 0
CEF Translated packets: 52, CEF Punted packets: 0
Expired translations: 16
Dynamic mappings:
— Inside Source
[Id: 5] access-list 88 interface FastEthernet0/1 refcount 5
Appl doors: 0
Normal doors: 0
Queued Packets: 0
Router1#show ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.0.1 – c219.3460.0000 ARPA FastEthernet0/0
Internet 192.168.0.2 2 0050.7966.681a ARPA FastEthernet0/0
Internet 200.200.200.1 30 c21b.335c.0001 ARPA FastEthernet0/1
Internet 200.200.200.2 – c219.3460.0001 ARPA FastEthernet0/1
Sample Debug:
*Mar 1 01:34:56.483: NAT: address not stolen for 192.168.0.2, proto 1 port 62309
*Mar 1 01:34:56.483: mapping pointer available mapping:0
*Mar 1 01:34:56.487: NAT: creating portlist proto 1 globaladdr 200.200.200.111
*Mar 1 01:34:56.487: NAT: [0] Allocated Port for 192.168.0.2 -> 200.200.200.111: wanted 62309 got 62309
*Mar 1 01:34:56.487: NAT*: i: icmp (192.168.0.2, 62309) -> (200.200.200.1, 62309) [26099]
*Mar 1 01:34:56.491: NAT*: i: icmp (192.168.0.2, 62309) -> (200.200.200.1, 62309) [26099]
*Mar 1 01:34:56.491: NAT*: s=192.168.0.2->200.200.200.111, d=200.200.200.1 [26099]
*Mar 1 01:34:56.495: NAT: installing alias for address 200.200.200.111
*Mar 1 01:34:58.491: mapping pointer available mapping:0
*Mar 1 01:34:58.491: NAT: [0] Allocated Port for 192.168.0.2 -> 200.200.200.111: wanted 62821 got 62821
*Mar 1 01:34:58.495: NAT*: i: icmp (192.168.0.2, 62821) -> (200.200.200.1, 62821) [26100]
*Mar 1 01:34:58.495: NAT*: i: icmp (192.168.0.2, 62821) -> (200.200.200.1, 62821) [26100]
*Mar 1 01:34:58.495: NAT*: s=192.168.0.2->200.200.200.111, d=200.200.200.1 [26100]
*Mar 1 01:35:00.663: mapping pointer available mapping:0
*Mar 1 01:35:00.663: NAT: [0] Allocated Port for 192.168.0.2 -> 200.200.200.111: wanted 63333 got 63333
*Mar 1 01:35:00.663: NAT*: i: icmp (192.168.0.2, 63333) -> (200.200.200.1, 63333) [26101]
*Mar 1 01:35:00.667: NAT*: i: icmp (192.168.0.2, 63333) -> (200.200.200.1, 63333) [26101]
*Mar 1 01:35:00.667: NAT*: s=192.168.0.2->200.200.200.111, d=200.200.200.1 [26101]
*Mar 1 01:35:02.731: mapping pointer available mapping:0
*Mar 1 01:35:02.731: NAT: [0] Allocated Port for 192.168.0.2 -> 200.200.200.111: wanted 63845 got 63845
*Mar 1 01:35:02.731: NAT*: i: icmp (192.168.0.2, 63845) -> (200.200.200.1, 63845) [26102]
*Mar 1 01:35:02.735: NAT*: i: icmp (192.168.0.2, 63845) -> (200.200.200.1, 63845) [26102]
*Mar 1 01:35:02.735: NAT*: s=192.168.0.2->200.200.200.111, d=200.200.200.1 [26102]
*Mar 1 01:35:04.727: mapping pointer available mapping:0
*Mar 1 01:35:04.727: NAT: [0] Allocated Port for 192.168.0.2 -> 200.200.200.111: wanted 64357 got 64357
*Mar 1 01:35:04.727: NAT*: i: icmp (192.168.0.2, 64357) -> (200.200.200.1, 64357) [26103]
*Mar 1 01:35:04.731: NAT*: i: icmp (192.168.0.2, 64357) -> (200.200.200.1, 64357) [26103]
*Mar 1 01:35:04.731: NAT*: s=192.168.0.2->200.200.200.111, d=200.200.200.1 [26103]
[…] Here is the sample NAT configuration on Cisco Routers –> NAT Configuration on Cisco Routers (Static, Dynamic and NAT Overload) […]